
Just as the Equinox data breach seems to finally be on its way to being settled, Capital One gets hit with a massive data breach. In 2019, data is no longer just personal information: it’s a commodity that hackers want to steal and sell. For companies who are entrusted with keeping any kind of personal data safe, from the massive amount of data stored by hospitals to any human resources office,keeping the network secure is no longer optional: it is vital (and network diagrams/documentation are a key to network security).
In Europe, the General Data Protection Regulation (GDPR) has been enacted for just over a year. For organizations, this means that ‘controllers of personal data must put in place appropriate technical and organisational measures to implement the data protection principles’.
In the United States, regulations are starting to churn out on the state level. The California Consumer Privacy Act (CCPA) enhances data privacy protections for California residents, and puts pressure on organizations to keep the network secure. For example, in the CCPA, there are stipulations that, “…become victims of data theft or other data security breaches can be ordered in civil class action lawsuits to pay statutory damages between $100 to $750 per California resident and incident, or actual damages, whichever is greater, and any other relief a court deems proper, subject to an option of the California Attorney General’s Office to prosecute the company instead of allowing civil suits to be brought against it. (Cal. Civ. Code § 1798.150)”
The State of Ohio recently passed legislation that corporations must take all reasonable measures to protect customer data. Colorado’s Consumer Data Privacy Act, which Colorado lawmakers billed as the nation’s strongest, tasks organizations to take ““reasonable” steps to protect the personal information they keep.” The Colorado law notes that using a third-party data management firm doesn’t exempt organizations from responsibility in the case of a data breach.
With states such as California, Colorado, and Ohio enacting data privacy laws, more and more states will likely soon follow suit — and, as data continues to be treated as a valuable commodity, the need to secure it and protect it from hackers will only continue to rise.
As a result, many organizations are scrambling to protect themselves…if, however, you don’t know what is in your network in the first place, how can you secure it?
Network documentation and network diagrams not only help you solve troubleshooting issues faster (or avoid them in the first place) and reduce waste…they help you secure the network.
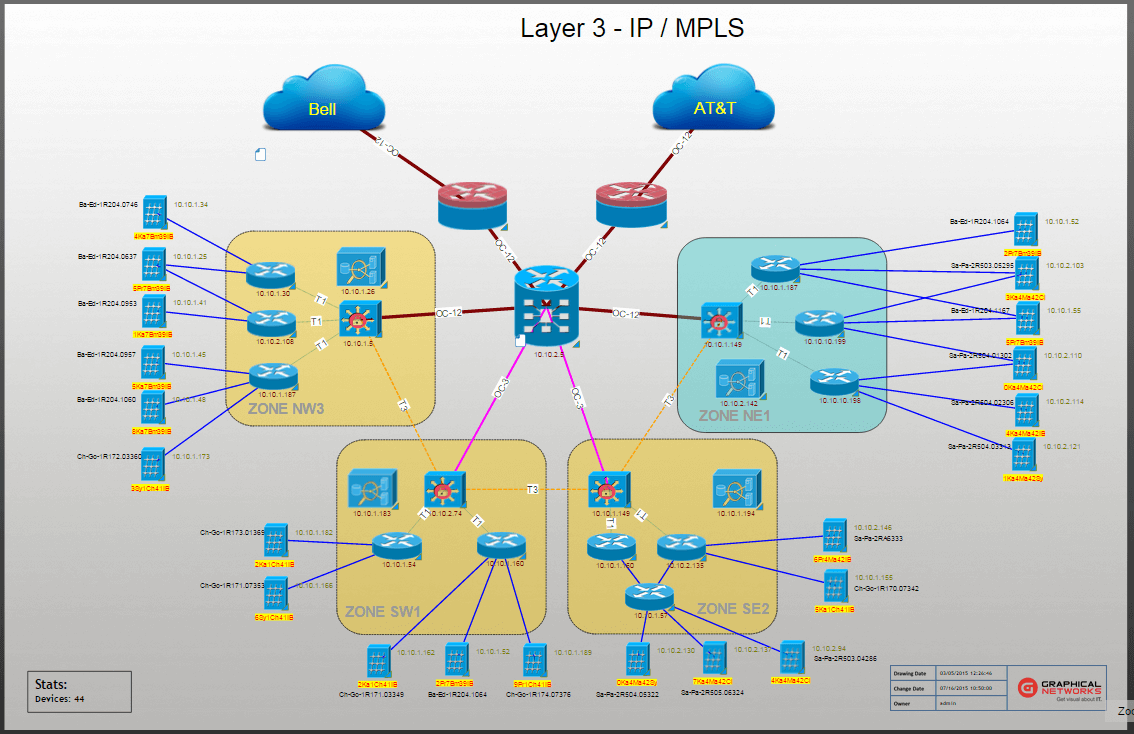 Example of a logical network diagram in netTerrain
Example of a logical network diagram in netTerrain
In fact, documenting the network is so essential to proper network security that it’s written into the executive order ‘Improving Critical Infrastructure Cybersecurity’ that was issued by POTUS back in 2013 (a voluntary framework meant to reduce security risks to infrastructure and reduce the impact of network attacks on the US economy, business, and government). One of the main tenets of this order is identification…and, particularly, to ‘identify both physical and software assets within your organization in order to establish a program for asset management’.
WIth network diagrams and automated network documentation software such as netTerrain, you can know where your network assets are and what’s connected to what. Know, for example, which versions of software your devices are running and if they need any patches that have been issued, the VPN connection points (plus links and/or failover connections)…and much more.
Networks are always changing, and documenting the network using a lo-fi tool such as Excel or Visio doesn’t cut it if you want to secure the network. Using an automated solution, you don’t just diagram the network once and call it done: you ensure your network stays up-to-date as it changes.